1. cipher 基础
在Kernel crytographic 的cipher 还有如下几类:
- ablkcipher_tfm(asynchronous multi-block cipher transform)
- blkcipher_tfm(synchronous multi-block cipher transform)
- cipher_tfm(Single block cipher transform)
更为安全的是使用ahead 加密形式, 可以见此篇文章。什么是AEAD加密
在kernel中cipher 都为skcipher(Symmetric Key cipher, 对称性加密算法)
后面我们以kernel/drivers/crypto/atmel-aes.c 进行分析ablkcipher 的驱动。
2. cipher alg register
atmel aes 驱动初始流程可见下图: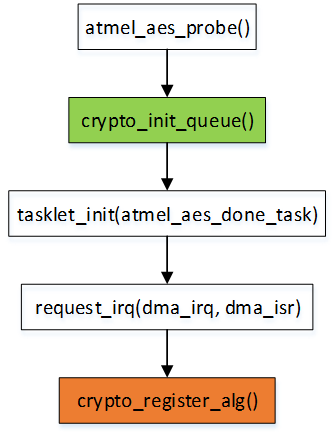
1 | static struct crypto_alg aes_algs[] = { |
2. encrypt flow
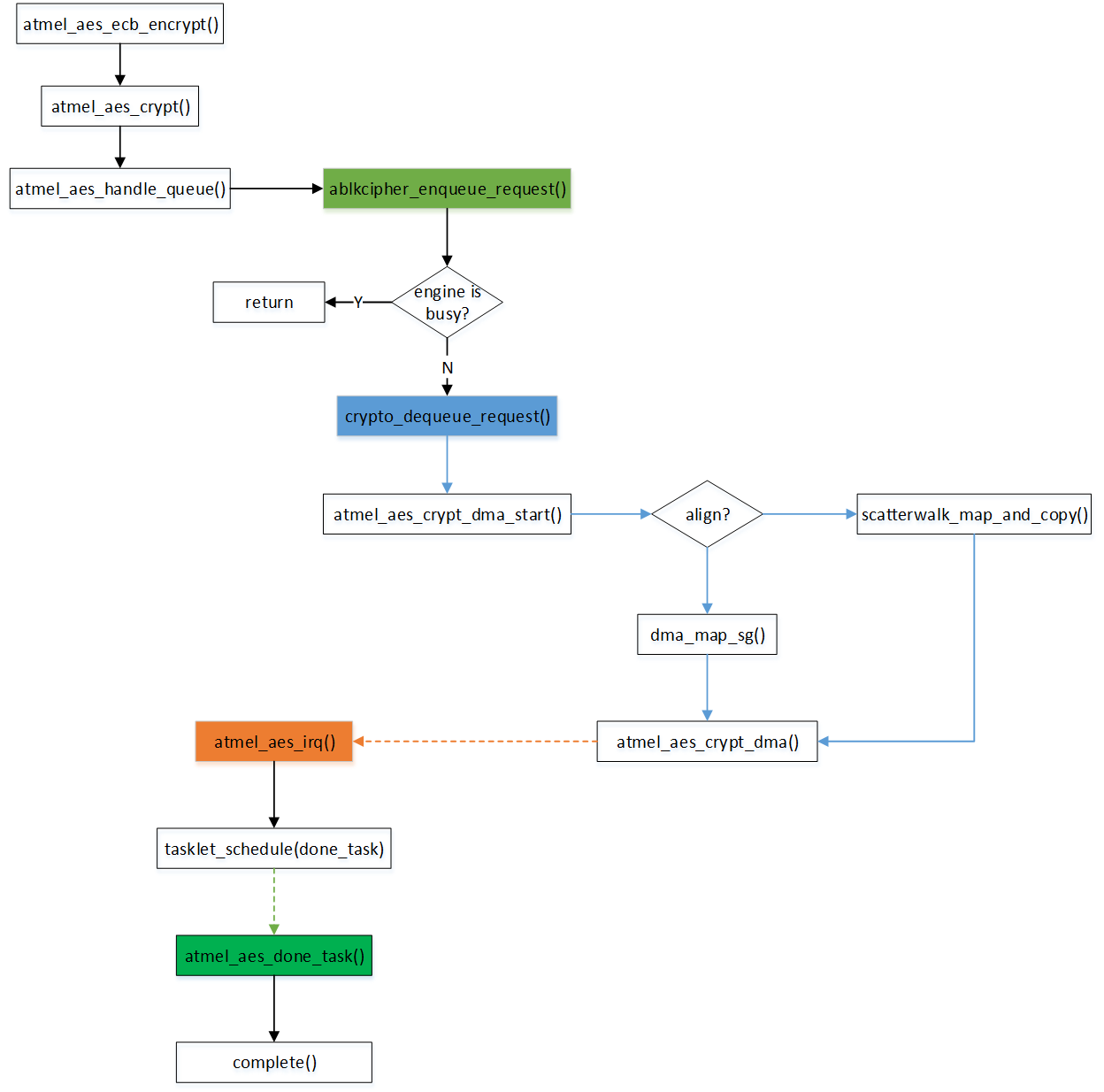
每当encryp 时, 我们将使用ablkcipher_enqueue_request()
把ablkcipher_request *req 添加到队列上。在判断HW engine 是空闲可用时,再从queue 上取出并进行HW 的加解密操作。decrypt 的流程如此类似,区别在于设定HW 的mode 设定。
2.1. data structure
1 | struct crypto_queue { |
在中断完成后,atmel_aes_done_task()-> atmel_aes_finish_req() -> req->base.complete(&req->base, err) 这样会调用到complete() 完成函数,实现了异步的通知行为。
1 | static void atmel_aes_done_task(unsigned long data) |
我们可以参看kernel/crypto/testmgr.c 中的测试代码,它的使用案例。
init_completion(&result.completion);
ablkcipher_request_alloc(tfm, GFP_KERNEL);
ablkcipher_request_set_callback(req,CRYPTO_TFM_REQ_MAY_BACKLOG, tcrypt_complete, &result);
crypto_ablkcipher_clear_flags(tfm, ~0);
crypto_ablkcipher_setkey(tfm, template[i].key, template[i].klen);
ablkcipher_request_set_crypt(req, sg, sgout, template[i].ilen, iv);
crypto_ablkcipher_encrypt(req);
crypto_ablkcipher_decrypt(req);
1 | static void tcrypt_complete(struct crypto_async_request *req, int err) |